Zero Slack.
Qualified Threats.
Adaptive Controls.
Seceon Open Threat Managment Platform
Seceon’s OTM Platform makes the best out of available information and intelligence from various digital assets – guided by ML based behavioral analytics and AI based decision-making – to raise and eliminate only the qualified cyber security threats, proactively and confidently.
Average no. of days to identify breach
IBM Data Breach Report (2020)
%
Organizations without Incident Response plan
Cybint Cyber Security Facts and Stats (2020)
%
Security Leaders anticipating critical infrastructure breach
Black Hat USA Survey 2019
The Problem with Siloed Security Solutions
- Significant redundancy of threats and alerts causing alert fatigue
- Lacks comprehensive datapoints for accurate threat detection
- Operational hassle with disparate dashboards from various tools/ platforms
- High cost of integration, support and maintenance
Seceon’s Open Threat Management Platform is built organically with 360° perspective on cyber security, eliminating the pain, redundancy and disparities associated with bolt-on siloed solutions.
Real-time Processing at Speed
Get actionable intelligence at real-time processing speed with Big/Fast Data technology based on in-memory compute.
Built-in Correlation based on Behavioral Patterns
Let user, entity and network behavior analytics and anomalies shape up event correlation to generate reliable Threat Indicators.
Dynamic Threat Models for Attack Analysis
Harness the power of AI based compute to generate threat models mirroring attack techniques and tactics depicted in MITRE ATT&CK Framework.
By leveraging cutting edge technologies, the platform brings best-of-breed cyber threat detection techniques, visualization, remediation and reporting with 75%-90% reduction in Capex and Opex.
Seceon’s Open Threat Management Platform strikes a fine balance between automation, visibility, insights and custom controls. OTM optimizes analytics, reduces time-to-detection, time-to-remediation and provides control mechanisms to enforce network policies for micro-segmentation and custom user-defined-alerts.
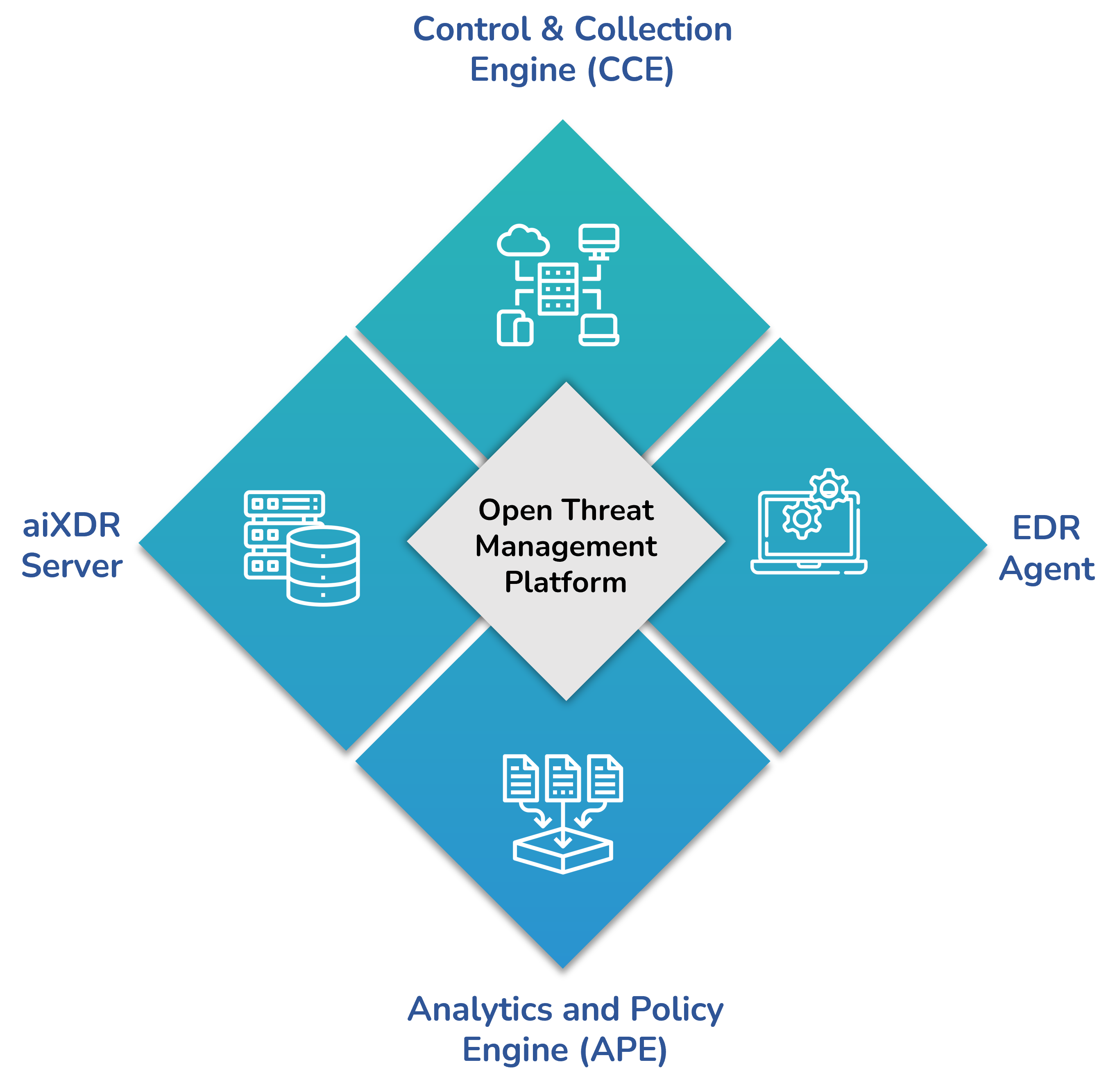
Seceon OTM
Key Components
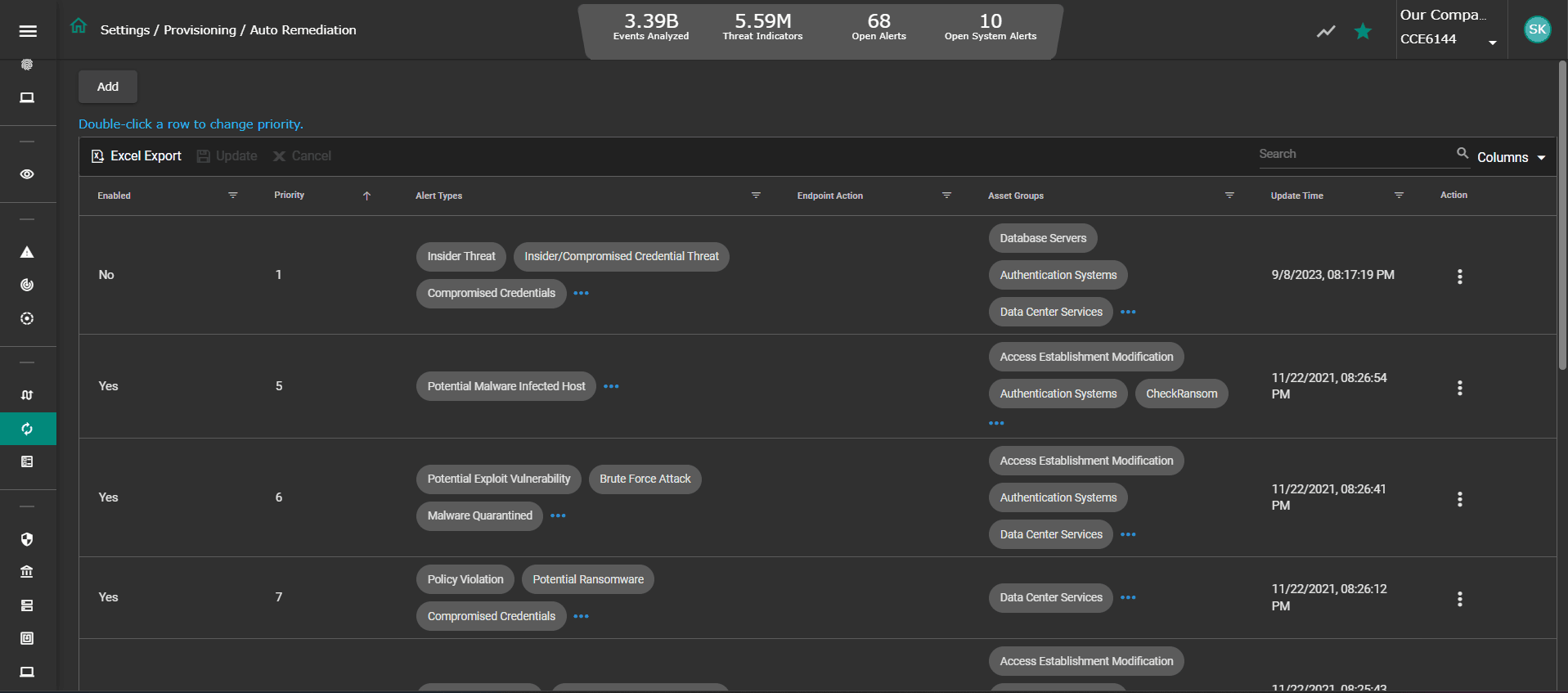
- Control & Collection Engine (CCE)
The CCE orchestrates a collection of events and network traffic data across assets deployed within the enterprise and cloud. It applies intelligent detection for enrichment of structured and unstructured data before routing to the OTM core through a secure connection.
- Analytics and Policy Engine (APE)
The APE forms the core of OTM and processes high-volume high-velocity data in real-time, while feeding threat intelligence, behavioral anomalies, historical context and vulnerability scan results to dynamic threat models driven by actionable AI and ML based correlation. Remediation routes can be selected with minimal intervention or full automation for threat containment.
- EDR Agent
The lightweight agent resides on each endpoint with the objective of gathering specific information on applications, processes, file events, executables, user access, telemetry etc. Also, it renders threat containment and elimination on the endpoint triggered by remediation policy.
- aiXDR Server
The aiXDR Server orchestrates data collection across each tenant, in a multi-tenant environment and relegates specific instructions to the aiXDR agents in communication with the APE.
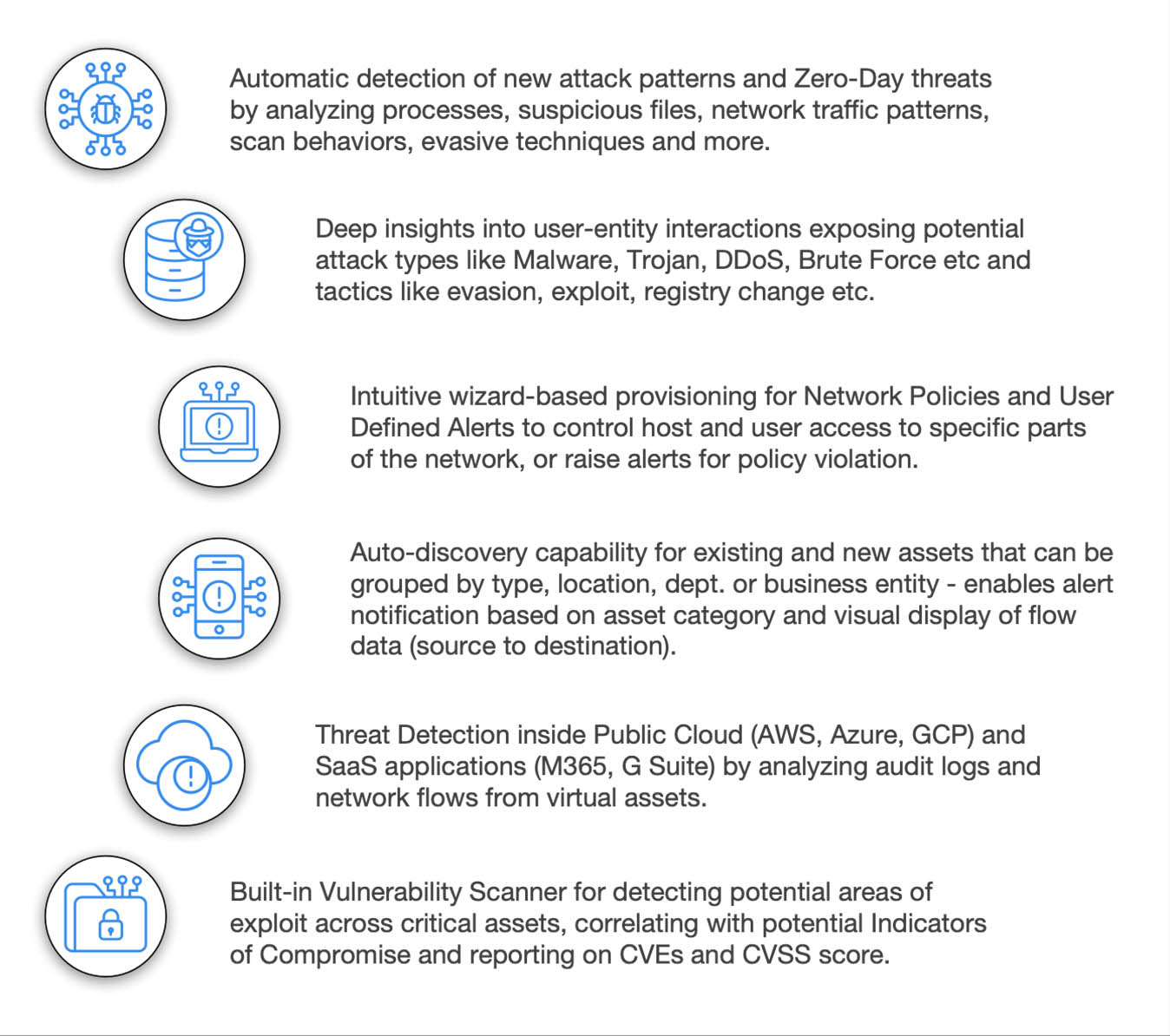
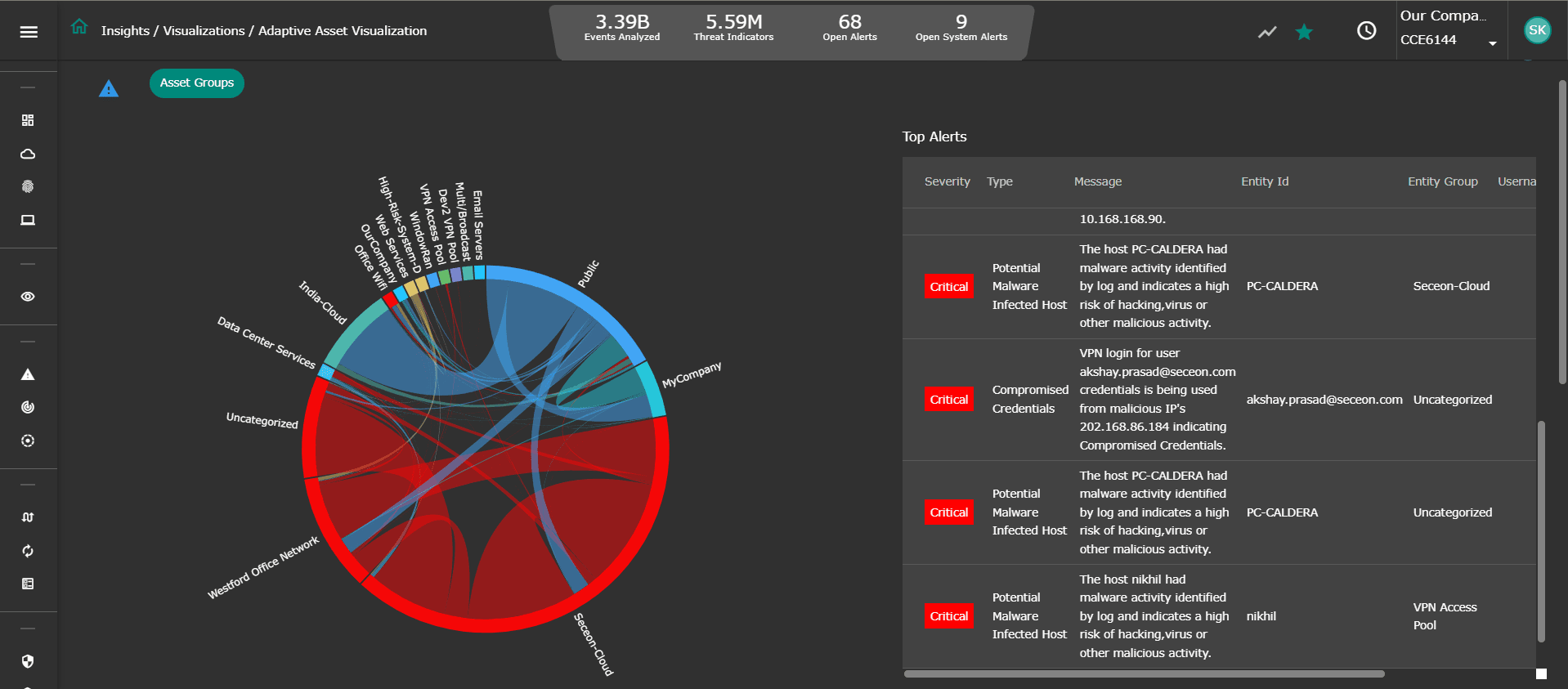
Threat Hunting with Deep Tracker™
Dive deeper into threat indicators correlated and analyzed through dynamic threat models, irrespective of the source (network, host, device, ML) and drill down into the actual event with rich contextual data (Event Type, Source, Host, Destination, User Name etc) synthesized in an easy-to-read format.