Ransomware is a type of malware software or files designed to block access to a computer system until a sum of money is paid. While basic ransomware simply locks the machine without destroying any files, more sophisticated virus employs a method known as cryptoviral extortion. Unless ransomware, it attempts to publish/modify and defame the victim’s personal data or prevent access to it.
Some simple ransomware locks the system without damaging any files. Still, more advanced malware versions uses a technique called crypto viral extortion. Here you can get a lock screen blocking your access and demanding a ransom.
Definition of Ransomware Detection Software
Ransomware detection software is designed to notice common indicators of ransomware, then block these attempts through data encryption. Ransomware detection notifies you when your files have been attacked and guide you through the process of restoring your files. Ransomware is a type of malicious software (malware) designed to block access to your files until you pay money.
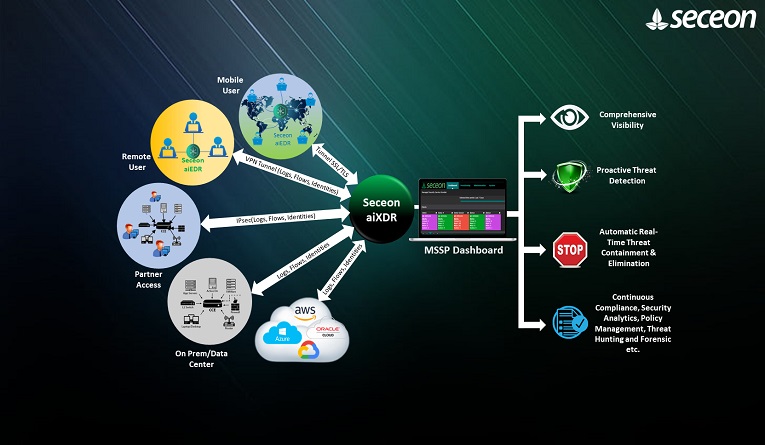
How It Works
The cost and impact of cyber-attacks resulting in data theft or destruction have become staggering. With the rate at which cybercriminals can attack organizations and infect their computer systems, it is no wonder ransomware is a widely used technique for these malicious actors to make a profit.
Ransomware is a type of malware program that encrypts data on local or networked computer systems and demands that the user pay for its release. It is a type of malicious software.
Ransomware locks up access to data on a computer network and informs the victim they can regain access only after making the ransom payment, usually payable via some untraceable method, also referred to as online blackmail, demanding bitcoin payments in response to being blocked from accessing information considered valuable or critical for business purposes.
Examples of Ransomware Detection Software Tool
Ransomware is becoming a popular form of hacking. Many companies affected by ransomware demand to be brought around with the help of self-take measures.
The latest string of Japan has become £260,000 ransom case. It apparently pay threat level city hall 36 department including email address, municipal laboratory systems and crime data bases on behalf applying their technical departments states hard-drive services at local offices.
Benefits of Early Ransomware Detection and Response Tool
There are two sides to the coin when it comes to decrypting or stealing data. This has been an ongoing topic of concern for most cyber security professionals.
Once a hacker finds a way into your computer, what do they do with your files and how can we detect them? Threat protection differs vastly by industry. Each executive and even personal computer has unique needs that often times require customized solutions where multi-layered software is necessary to suit the technician’s needs.
It is necessary to implement security assurance controls. Be able to protect the stability of operations and transactions are carried out securely and safely even if there was a serious data theft or system hijack due to the presence of an adequate operation ecosystem, including facilities like disaster recovery (backup), encryption software solutions, and anti-ransomware operational systems.
Losses You Can Avoid
Do you remember the summer of 2013 when the WannaCry ransomware attack completely shut down large parts of Western Europe? Yeah, it was a really, really bad time. In fact, back then, in the summer of 2013, it was one of the most serious ransomware attacks ever seen. Ever!
Seceon Inc. understands that without a clear sense of how to detect and recover from such an attack, your business could lose money on the initial ransom demand and future profits if you have to take time away from growing your operation.
Infected and lost your data? It would be best if you considered ransomware protection. In recent years, ransomware attacks have become more common as cybercriminals use malware to extort money from their victims. Here’s why.
Yes, purchasing and distributing trusted shareware and applications breaches copyright laws, but it is not quite a criminal activity.
On the other hand, ransomware attacks used with malicious intent can be devastating for businesses of any size or industry—and the damage costs are in the billions. In this post, we will talk about ransomware detection, types, and prevention.
Every once in a while, something comes along that is simpler and more effective than the last thing. This is the case in the world of ransomware. While the good old days of data backups are likely lost to the ravages of time, the ransomware landscape is not what it once was.
Kinds of Ransomware Detection Tool You May Come Across
When you can identify an attack, your information will be more secure. There are three essential ways of identifying ransomware: signature, behavior and unusual traffic.
- Signature
Every malware has a mark made out of data like domain names, IP addresses and different pointers that recognize it. Signature-based detection utilizes a library of these marks to contrast them with documents running on a machine. This is the essential technique for identifying ransomware.
Ransomware creators can make novel forms of malware with new marks for each assault. Signature-based identification cannot distinguish what it does not perceive. This leaves frameworks powerless against each new malware variation.
- Behavior
Ransomware acts in a strange manner: it opens many records and replaces them with scrambled renditions. This technique for identification can assist clients with remaining protection against other normal cyberattacks.
- Abnormal Traffic
Strange traffic is an expansion of identification. It works at the organizational level. This prompts big-data transfer to outside frameworks. Complex ransomware attacks are frequently twofold: they encrypt information to deliver, yet they take information prior to scrambling it to use as an additional influence.
While ransomware can cover its tracks and hide the exchanges, it might make network traffic that can be followed. Unusual traffic can follow back to the ransomware on the machine so clients can erase it.
Ransomware is constantly evolving, and the exponential growth of malware has been inescapable. Further, those who are not keeping up with the latest ransomware may want to start. This content will highlight the five ransomware types and the general prevention methods.
Ransomware is not a new threat to the enterprise, but the number of attacks, significantly since 2018, has increased dramatically.
While ransomware is an ever-present threat to your day-to-day operations, there is good news! Give us a call today to get the latest ransomware tactics and strategies.
The popularity and prevalence of different types of ransomware continue to grow. Whereas ransomware used to be mostly a one-time event on your network, with Seceon, you never have to worry about somebody getting hold of your data.
Here Are The Types of Ransomware Detection Tool
- Crypto Ransomware
The most common type of ransomware, it encrypts the files and complete data within a system. It makes content inaccessible without a decryption key. With this, attackers often blackmail a user and do not provide a decryption key after paying the ransom.
- Lockers
What if you are locked out of your home entirely, and there is a telling sign hanging on your door whether to pay the asked ransom or watch your place go in flames? Here, you are locked out of your system, and a lock screen displays a countdown clock and ransom demand.
- Scareware
The second most common is the scareware. As the name suggests, it makes you install fake software that claims to have detected a bunch of viruses and other complex issues on your computer. After installation or before, it could lock your computer or flood the screen with pop-up alerts without actually doing any harm.
- Leakware
A serious and destructing form of ransomware is the leaking ware. If it infects your system, it threatens to distribute sensitive personal or company information online. It could show you the fake illegal files in your system and threaten you with jail time. It creates panic and often prevents the victim from acting rationally in any way possible.
- Ransomware as a Service
RaaS is a malware hosted anonymously by a hacker that handles everything from distribution, payment collection, and restoring access for a fee of the loot. This person or handler could be anyone helping the attackers for a good amount of extortion money.
Take a note that ransomware is a new form of threat that has made headlines for stealing millions of dollars and affecting some of the world’s most popular brands.
Here are some tips you should follow –
- Let us implement and enhance email security;
- Let us harden endpoints access;
- Let us restrict access to the software management server;
- Let us implement the anti-malware program in your systems;
- Let us develop and pressure-test incident response plan;
- Let us help you practice better IT department.
In conclusion, we are living in uncertain times. It can be challenging to figure out the next big thing. Would you believe us if we told you that one of the hottest topics right now is ransomware detection? After all, ransomware is the new normal. It is the new digital crime. It is not just harmful to the unlucky souls who fall victim; it has a global impact on companies, their infrastructure, and the markets.