The US largest pipeline is managed by the Colonial Pipeline, which shut down on May 7, 2021 temporarily due to the Cyberattack attempted by the Cybercriminals. The all sudden shut down of computing system affected the IT infrastructure too. The shutdown was over the entire gulf and east coast which created lot of chaos all over the region due to inability of getting service. The pipeline has large span covering 5500 miles which carries millions of gallons fuel per day. As per the FBI investigation it was attempted by the DarkSide Group, which is believed to operate from Eastern Europe or somewhere from Russia.
The situation became critical, the President Biden came in action and assured people that it will be fixed soon but people have to support rather than hoarding it out as the entire process of colonial is not just a on-off process ,it will take time for oil and gas to move over the large span of 5500 miles and stable the system movement.
How it was Attempted
Ransomware Attack was implemented on the computing equipment. Reports mention before the day of actual attack malware was injected on the system. And on the very next day it resulted into Ransomware, which indicates the process was initiated in multi-steps.
The moment attack occur the entire system got encrypt and started demanding for Ransom, the colonials were asked to send money earliest otherwise they would public the data on web. The colonial official managed earliest by paying a rough equivalent of $5 million, which was taken in non-state currency to what we call Bitcoins. Colonial Paid around 75 bitcoins.
“The Whitehouse person, when asked for a confirmation whether the company has paid the ransom or not made statement it’s not a good idea to pay ransom as it’s coming up like a business to hack the system and make money.”
The moment the ransom was paid the hacker provided the software key to restore back data, but it started very slowly. The entire processing and recovery became very slow and it took more than expected time to recover back. It was announced to take a week time to return back to normal.
The colonials are not the only cases but many cases occurred recently whether we say for SolarWinds case, Microsoft or the one that occurred with US police are all where they were asked for huge ransom.
Though the Ransom was paid, restoration process got initiated but here the problem didn’t ends up. it’s actually pointed out to think it does not gives any surety that they won’t be attacked again. The ways, process, and step of attack they will keep on changing and affecting the system again and again in known and unknown way. Using a solution that would help to just come out from the current problem won’t be a good idea in this way you have to always look on new things as per the new hurdles that will come while dealing with data security.
The solution should be like, prepared for all known and unknown kind threat attempt whether it get initiated within or outside the system. It should have 360 degree visibility and comprehensive approach that should help to know in and out of system and able to answer all queries of how, what, when and why.
In all of the cases that occurred each were left with some or other backdoor which was found by hackers.
What is Required?
The ultimate approach that is required to come out of problem raised above would be a solution that does everything in a single click and that is something what Seceon is ,it’s not only a cyber security solution like the other existing one but a solution that truly follows the comprehensive approach and work to provide the Seamless solution with good user experience.
Seceon aiSIEMTM and aiXDRTM enables organization to have complete visibility of system, quickly and clearly before malicious process initiate and reach to some extensive damage to business. Its industry’s first and only fully automated threat detection and remediation system. It does detection in the early stage itself, generate the necessary alert as per the monitoring of activities and advanced corelation that is in-built in Seceon’s Platform. It easily diagnoses both the known and unknown threat and define alert with “Continuous real time monitoring, Proactive Threat detection, auto stopping of threat and breaches in Real-Time”. It’s an agentless, behaviour-based solution with extensive dynamic threat model, excellence of machine learning, artificial intelligence and Big Data. The platform is based on lambda, micro-service architecture.
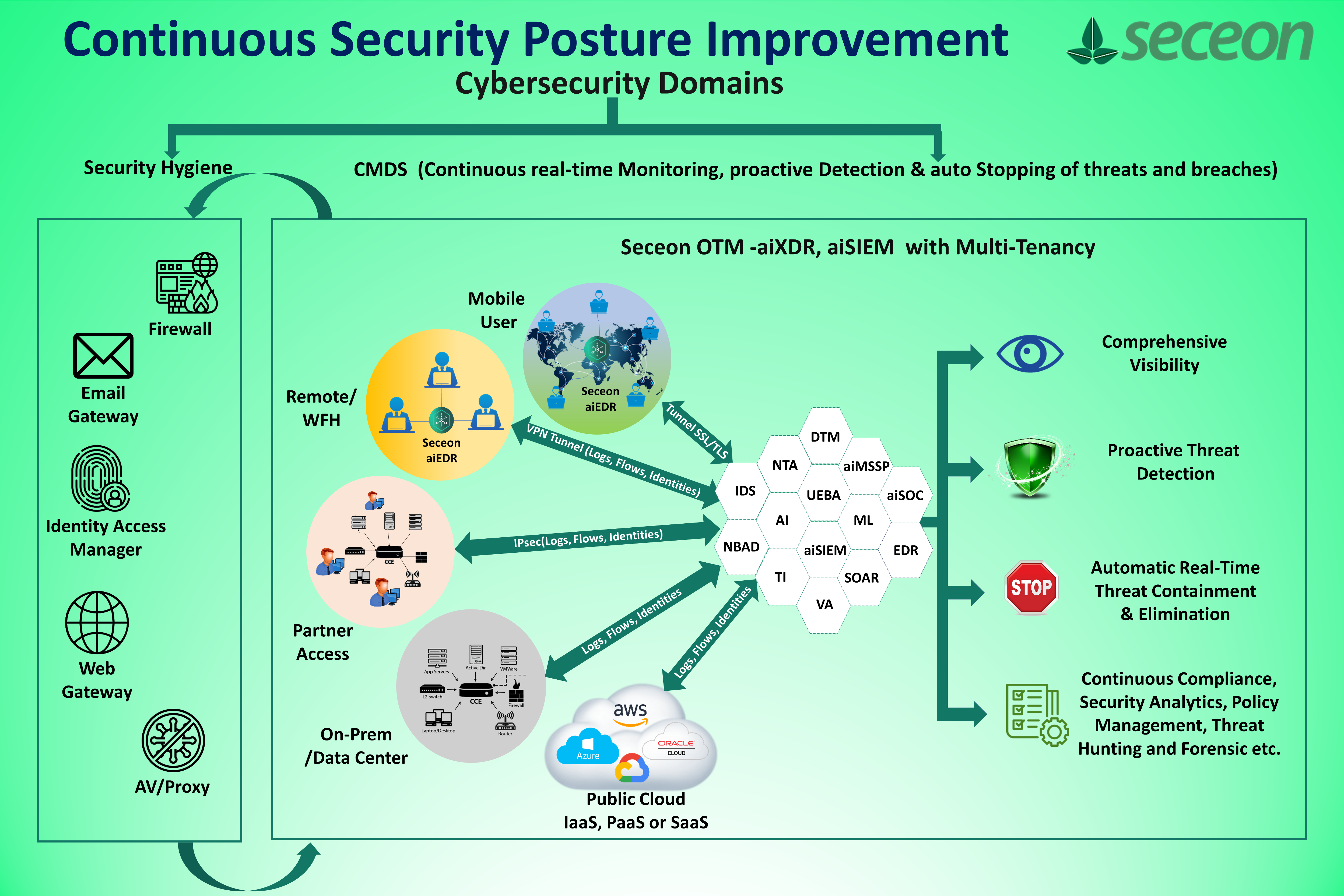
Diagram shows CMDS Approach (Continuous real time monitoring, Proactive Threat detection, auto stopping of threat and breaches in Real-Time)
It eliminates the use of multiple silos, which is complex to handle and corelate, to draw meaningful information. It has both push button and auto-remediation policy which make remediation simple and easy. Small to large all size organization can have it in their environment. We have around 4400+ deployments all over the globe.










