Sometimes it seems that MSPs (Managed Service Providers) have seen it all – from being the first company to place a PC on the desk of the local accountant, to connecting offices to the internet and running email servers to enabling office workers with OneDrive in Microsoft 365. Hardware, software, and users have been on a journey enabled by faster compute, cheaper storage, and higher user knowledge and expectations.
However, with anything good comes the bad, and MSPs have been fighting to protect their clients and users for decades. Even before networked computers and the internet, we saw many methods of computer viruses and worms spreading, disabling PCs, and frustrating users and technicians.
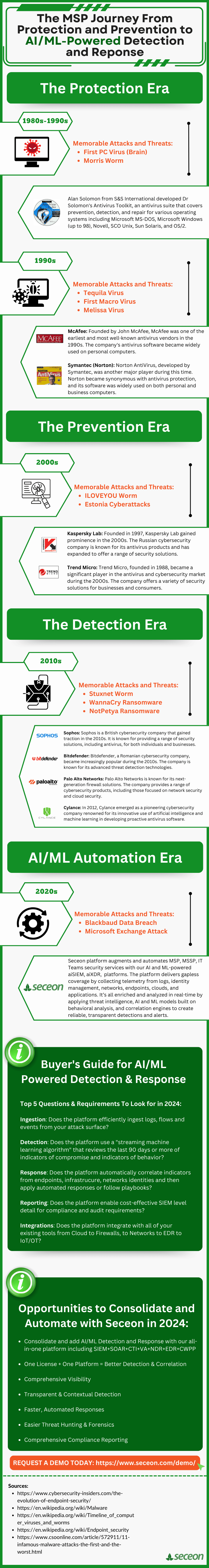
The First Viruses
Even before there were MSPs, the concept of computer viruses emerged in the 1960s and 1970s. The first known computer virus, called “Creeper,” was detected in the early 1970s on ARPANET, the precursor to the modern internet.
The first known computer virus is widely considered to be the “Creeper” virus. Creeper was a self-replicating program that appeared in the early 1970s on the ARPANET, which was the precursor to the modern internet. It was not created with malicious intent but rather as an experiment to demonstrate the concept of a self-replicating program.
Creeper spread between DEC PDP-10 computers running the TENEX operating system. When it infected a system, it displayed the message: “I’m the creeper, catch me if you can!” The virus didn’t cause any harm to data but demonstrated the potential for self-replicating code.
To counteract Creeper, a program called “Reaper” was created. Reaper was designed to remove the Creeper virus from infected systems. This early encounter with computer viruses laid the groundwork for the development of antivirus and cybersecurity measures in the years that followed.
The Protection Age Begins
In the 1980’s, the explosive growth of the PC and Microsoft DOS kicked off the modern era of PC viruses often spread through floppy disks and/or a compromised BIOS. It’s widely accepted that the first virus for MS-DOS was the “Brain” and in response, Alan Solomon of S&S International created “Dr. Solomon’s Anti-Virus Toolkit” in 1988.
The 1990s saw a significant increase in the number and complexity of malware threats. This led to the development of commercial antivirus solutions by companies like McAfee and Norton (Symantec). These products became popular as personal computing became more widespread.
McAfee, founded by John McAfee was one of the earliest and most well-known antivirus vendors in the 1990s. The company’s antivirus software became widely used on personal computers.
Symantec Norton AntiVirus, developed by Symantec, was another major player during this time. Norton became synonymous with antivirus protection, and its software was widely used on both personal and business computers.
1994 marks the year that the internet, the world wide web, and when email started to be consumerized. Business use cases for the internet started to be widely explored, and as MSPs connected offices to the internet there was no doubt that viruses like the Melissa Virus and other Macro Viruses would spread rapidly around the world.
The widespread adoption of the internet during and after the “Dot-Com” bubble and corporate use of email in the 2000s brought new challenges. Worms and other forms of malware spread rapidly through these channels. Antivirus companies expanded their offerings to include features like email scanning and firewalls.
Many MSPs may remember Trend Micro: Trend Micro, founded in 1988, became a significant player in the antivirus market during the 2000s. MSPs in both the EU and USA might also remember the launch of Kaspersky Lab, founded in 1997, Kaspersky Lab gained prominence in the 2000s. The Russian cybersecurity company is known for its antivirus products and has expanded to offer a range of security solutions.
The Prevention Age Begins
The early and mid-2000’s saw malware become more sophisticated; traditional and signature-based detection methods proved insufficient. Antivirus vendors started incorporating heuristic analysis and behavioral monitoring to detect previously unknown threats based on their behavior rather than relying solely on known signatures.
The 2010’s saw the growth of Sophos, a British cybersecurity company that gained traction and is known for providing a range of security solutions, including antivirus, for both individuals and businesses. Another MSP favorite of this era is Bitdefender, a Romanian cybersecurity company, that became increasingly popular during the 2010s.
The Cloud Age and the Birth of Detection and Response
The mid 2010’s and now in the 2020’s cloud computing, is the new normal from SaaS applications, cloud-based productivity, and telephone systems. Anti-virus solutions began to leverage cloud-based databases for real-time updates and threat intelligence, and then, with the growth of ransomware, endpoint security solutions became more comprehensive, encompassing not only antivirus but also features like intrusion prevention and detection.
Enterprise companies like CrowdStrike, Carbon Black (now VMware), and Cylance (now Blackberry) became known for their cloud-delivered endpoint protection. They gained attention for their focus on endpoint detection and response (EDR) and threat intelligence. Even, Cisco and Palo Alto Networks started evolving their firewall solutions to combine endpoint and network protection.
MSPs may remember the growth of web application firewalls, next-generation firewalls, and solutions like Webroot. In the enterprise, several Network Detection and Response (NDR) services were launched to modernize the ability to detect threats on the network more proactively.
Microsoft itself significantly strengthened its security offerings, including Windows Defender Antivirus and the Microsoft Defender suite. With a focus on integrated security solutions, Microsoft has become a major player in the cybersecurity landscape.
Today’s AI/ML Powered Detection and Response
As compute got cheaper and knowledge of how to create and distribute malware grew, both state-sponsored and nefarious threat actors began using AI to rapidly morph their attack models to detect and block them from working. And with the growth of machine learning (ML) and artificial intelligence (AI) modern SIEM’s and XDRs began to evolve rapidly in the enterprise.
Today, it’s essential that MSPs have advanced algorithms to analyze patterns and behaviors, real-time detection of indicators of compromise, and the ability to identify, correlate, and mitigate new and evolving threats.
MSPs are evolving their cybersecurity strategies from a traditional focus on prevention and protection to detection and response which is both proactive and a recognition that advanced cyber threats are increasingly sophisticated and can often bypass traditional preventive measures.
MSPs are investing in advanced threat detection and response technologies like Seceon. This includes the use of behavior analytics, anomaly detection, and threat intelligence to identify unusual patterns or activities that may indicate a potential security threat.
Cyber insurance providers and regulations like PCI 4.0 are pushing for modern AI/ML-powered SIEMs with real-time detection and automated responses to block stop or quarantine threats. Enterprise SIEMs and their complicated licensing and lack of multi-tenant and multi-tier support just don’t apply to the MSP business model.
Solutions like Seceon’s multi-tenant and multi-tier aiSIEM and aiXDR are cost-effective and risk-reducing and are increasingly required today by many industries and cyber insurance providers. MSPs are also recognizing the importance of collaboration and intelligence sharing within the cybersecurity community. Sharing threat intelligence and insights allows MSPs to stay informed about emerging threats and adopt more effective defense strategies. This has given rise to organizations like CompTIA’s ISAO, which is a central source for the MSP Community to stay informed and aware of emerging cyber threats.
MSPs are also placing greater emphasis on user training and awareness programs to educate clients about cybersecurity best practices. Well-informed users are less likely to fall victim to social engineering attacks, reducing the overall risk of successful cyber threats.
Overall, the evolution from prevention and protection to today’s AI/ML-powered ability to automate detection response at scale reflects a more proactive and adaptive approach to cybersecurity. MSPs are recognizing that only AI/ML-powered detection and response platforms provide the profit-margins and risk reduction to meet today’s threats and insurance and regulatory requirements.
Join over 350 MSPs and their 7,500 clients and learn how Seceon can modernize your cybersecurity program and increase your profit margins.